Now that HTTPS encrypts over 80% of web connections, powerful actors are targeting root certificate stores to compromise our security and surveil us. In the past year alone, that’s included a “market research” company secretly owned by Facebook and the government of Kazakhstan.
Forcing users to install a root certificate enables the certificate owner to decrypt almost all their Internet traffic. This capability is allowed primarily for enterprise network monitoring, and is becoming disturbingly popular in schools as well.
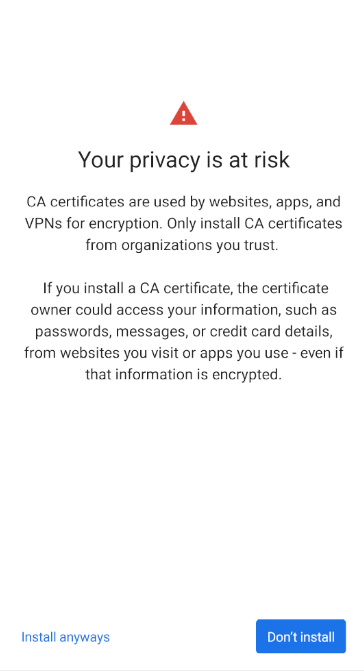
Amidst the increasing interest in compelling unsuspecting users to compromise their own encryption, we prompted OSes like Android and iOS to adopt more user-friendly dialogs to explain what’s really going on when you add a new root certificate.
In response, Android 11 is now rolling out significantly improved warnings and user interfaces for certificate management.
Why does this matter?
Certificates enable encryption, like in HTTPS. They tie a domain name (like eff.org) to a public key (a component used for end-to-end encryption). If the domain name is tied to the wrong public key, someone else can decrypt your Internet traffic, so your browser is designed to only accept certificates that are issued by certain trusted entities. Root certificates identify these trusted entities (like Let’s Encrypt) that can issue certificates for other websites.
Manually adding a new root certificate means giving the entity who created it the ability to make fake certificates (with the wrong public key) for every website you connect to. If that owner also has access to your network, they can get past the protections of HTTPS to decrypt nearly all of your Internet traffic.
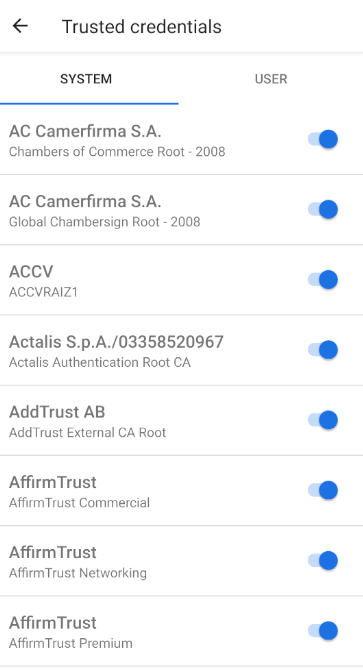
As encryption becomes more widespread, root certificates will have more power. It is paramount for end-user security that manually adding a root certificate be difficult and accompanied by sufficient and clear warnings. Furthermore, auditing the root certificates that are trusted by your device should be easier. After we wrote a blog post and filed a bug with Android calling on it to do better in these areas, Android 11’s release is leading the charge in user-friendly certificate management.
Firefox, Apple, and Windows, we’re looking at you next
The interface for adding and viewing trusted root certificates in iOS remains as clunky as it was last year. Other popular desktop OSes like macOS and Windows could use improvements, too. Firefox is unique from other browsers in that it maintains its own certificate store—which means it can improve as well. We implore Firefox, Apple, and Windows to improve their certificate warnings and management interfaces.