Our phones hold a plethora of important, private information about our personal lives, and it’s not just their contents that matter: the data that our phones exchange with cell towers during basic connection procedures can reveal critical, and private, information. Perhaps you called the suicide prevention hotline from the Golden Gate Bridge; maybe you received a call from the local NRA office while it was having a campaign against gun legislation, and then called your senators and congressional representatives immediately after. The contents of those calls aren’t as secret as you might hope to someone who knows that the calls were made, and when. And just knowing the location a phone was in at a certain time, regardless of whether a call was made, could place someone at a protest—or at the scene of a crime.
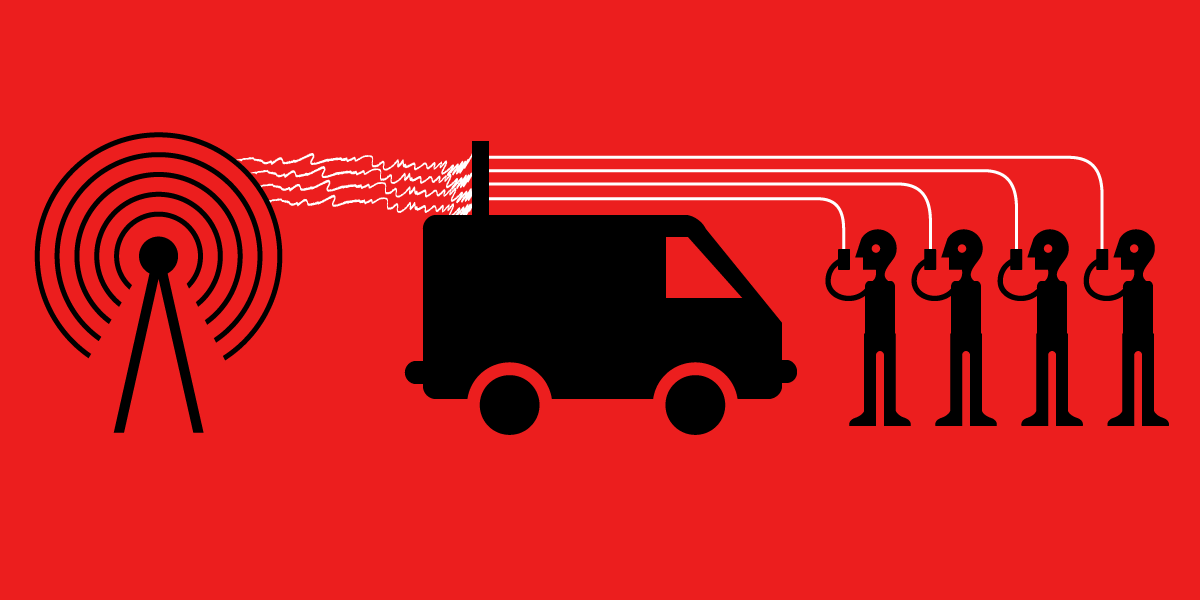
While the field of cell network security has been rapidly advancing, there’s also been a significant rise in the exploitation of cell network security bugs by criminals and law enforcement, who are using them to gain access to that private data. Devices known as Cell-Site Simulators (CSSs, a.k.a. Stingrays or IMSI-catchers) are increasingly being used by law enforcement for both dragnet and targeted surveillance; and several years ago we saw the first crackdowns against criminals using cell site simulators on a mass scale to deliver spam.
Rightly, there’s been a lot of interest in—and confusion about—what CSSs are capable of. From activists worried about being targeted and tracked, to policy makers concerned about the privacy of their constituents, to technologists interested in learning about the security flaws so that they can deliver fixes, there’s a range in knowledge, though all of these groups have a stake in learning more. But the barrier to entry to the field of cell network security has historically been quite high, even if you already have a technical background. While there’s increasingly more highly technical research into the cell network attack techniques that CSSs rely on, very little exists for the average reader.
To help bridge this gap, we’re publishing “Gotta Catch 'Em All: Understanding How IMSI-Catchers Exploit Cell Networks”, an in-depth white paper that explains some of the most relevant cell network attacks from the ground up. The white paper is entirely self-contained, and is meant to make accessible the technical details of the kind of attacks CSSs might rely on. While the contents will be most accessible to technologists, all readers should be able to gain a thorough understanding from it. The paper also addresses many common technical questions that come up when discussing the capabilities of CSSs, such as: what are the different kinds of location tracking attacks, what are the known limits around cell network communication interception, and how does all this actually work?
Given the prevalence of cell phones, these vulnerabilities—and the CSSs that take advantage of them—should not just be a concern for security researchers. We’re all vulnerable. The metadata and data that our phones exchange with cell towers during basic connection procedures is being taken advantage of by third parties to invade our privacy. Demystifying the tech behind these techniques is critical for raising awareness about the issue and finding solutions. We hope you’ll join us.